Here’s all you want to know about WannaCry Ransomware Cyber Attack: What and How?
Bitcoin Ransomware Cyber Attack is the burning topic now. It is deemed as the biggest ever cyber-attack in the Internet history. A ransomware named WannaCry stormed through the web.
On Friday, May 12, 2017, around 11 AM ET/3PM GMT, a ransomware attack of “unprecedented level” (Europol) started spreading WannaCry around the world. It used a vulnerability in Windows that allowed it to infect victim’s PC without them taking any action.
What is WannaCry?
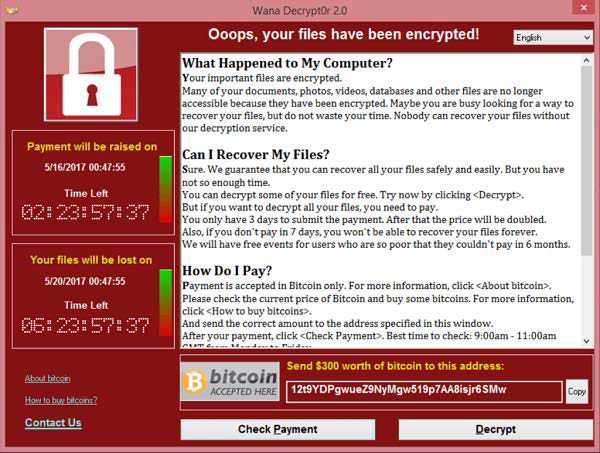
Wanna Decryptor or WannaCry or wcry is a Ransomware program that locks all the data on a computer system, encrypts them and then demands money to decrypt it. The user is left with only two files in their system – the next step and the Wanna Decryptor program itself.
But users should note that even after paying ransom amount there is no assurance that your data is safe and you’ll be able to retrieve it. The ransom is demanded in Bitcoins. The malicious software locks down victims’ systems and refuses to grant them access to their files unless they agree to pay at least $300 in bitcoin.
In the first few hours, 200,000 machines were infected. Big organizations such as Renault or the NHS were struck and crippled by the attack.
WannaCry Background – How does it work?
- Arrives via phishing email (PDF) and spreads like a worm using covert channels
- Payload delivered via exploit running as a service
- It performs encryption in the background, with key-built in
- Uses tor to stay anonymous
- Drops ransom notes in 25+ languages
- Encrypts shared and local files (176 types of files)
Do’s and Don’ts
- Do not open attachments in unsolicited e-mails, even if they come from people in your contact list
- Do not click on any URLs contained in an unsolicited e-mail.
- Report any suspicious emails or attachments to the IT/IS team.
- Do not download software, videos, MP3s, etc.
- Check that your antivirus is updated and running in any machine you are using.
- Backup your critical data periodically.
- Do not connect any smartphones or portables devices to company systems.
- If you Job Role involves connecting to remote systems and executing applications. Please remain alert if you get any notice about failed connection or unable to execute application/s. If connection/execution fails do not attempt again.
- If you believe your computer has been infected, immediately disconnect your machine from the network by pulling the LAN cable out of the port in your computer. Do not try to restore any data on your own.
How to safeguard yourself from Ransomware Attacks
Following are some of the effective ways through which you can shield your data from theft.
- Make safe and secure backups – One of the apt ways to protect your confidential data from Ransomware. You should make multiple backups –
- On the cloud
- Hard drive
It is wise to keep your data to an external drive, which is not connected to the internet; your data will be safe and secure.
- Keep your system updated – Download the latest version of a software. Update your system frequently; companies release software updates to fix the bugs and vulnerabilities that were present in the previous versions therefore keep your systems updated.
- Make use of antivirus software – Having antivirus will at least protect your data/system from the most basic, popular viruses/infections by scanning your files. Many of the antivirus software available today is equipped to prevent Ransomware from being downloaded onto computers.
- Educate yourself – Stay alert! While browsing any website, the address has “s” in the https. Also, never click on suspicious links or attachments. Administration should ensure that employees don’t have pointless access to parts of the network that is not related to their work. This could prevent your data from such hazardous attacks.
Stay Vigilant, Stay Safe!
Tags In
Subscribe For Updates
Categories
- Accountant
- AI
- Automation
- Awards and Recognitions
- Blue Collar Staffing
- Burnouts
- Campus Recruiting
- Cloud
- Co-Ops agreements
- Company Culture
- Compliance
- contingent workforce
- Contingent Workforce
- COVID-19
- Cyber Security Staffing
- Data Strategy
- Digital Transformation
- direct sourcing
- Distributed Workforce
- Diversity
- Diversity & Inclusion
- Economy
- Events & Conferences
- fleet industry
- Gig Economy
- Girls in Tech
- Global Talent Research and Staffing
- Government
- Healthcare
- Healthcare Staffing
- Hiring Process
- Hiring Trends
- Home Helathcare
- HR
- HR Practices
- HR Tech
- IT
- Labor Shortages
- Life Science
- Local Governments
- News
- Nursing
- Payroll Staffing
- Public Sectors
- Recruiting
- Remote Work
- Skill Gap
- SMB Hiring
- Snowflake
- Staffing
- Staffing Augmentation
- Staffing Challenges
- Talent ROI
- Tech Staffing
- Technology
- Tips & tricks
- Total Talent Management
- UI/UX Design
- Uncategorized
- Veteran Staffing
- Veterans Hiring
- Veterans Hiring
- Workforce Management
Recent Posts
- Automation in Recruiting: From Chatbots to Predictive Screening
- Gig Economy Expansion: The Impact on Talent Pools and Business Models
- Skills-Based Hiring: Why Credentials Alone Don’t Cut It in 2025
- Procurement 3.0: AI & Intelligent Automation in 2025
- Q3 Is Here: Is Your Contingent Workforce Strategy Falling Behind?
Newsletter
Archive
- September 2025
- August 2025
- June 2025
- April 2025
- March 2025
- December 2024
- November 2024
- October 2024
- September 2024
- August 2024
- July 2024
- June 2024
- May 2024
- April 2024
- March 2024
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- July 2022
- June 2022
- November 2021
- October 2021
- September 2021
- August 2021
- July 2021
- June 2021
- May 2021
- April 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- October 2020
- September 2020
- August 2020
- July 2020
- June 2020
- May 2020
- April 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- August 2019
- July 2019
- June 2019
- May 2019
- January 2019
- December 2018
- November 2018
- October 2018
- September 2018
- August 2018
- July 2018
- June 2018
- May 2018
- April 2018
- March 2018
- February 2018
- January 2018
- December 2017
- November 2017
- October 2017
- September 2017
- August 2017
- July 2017
- June 2017
- May 2017
- November 2016
- October 2016



